BotTROP Malware detection system based on the Novel Artificial Intelliigence algorithm
Content:
1. Overview
2. Unique features of bottrop
3. How does BotTROP work?
4. Where can BotTROP be most beneficial?
5. BotTROP - EDU
6. BotTROP - PRO
Overview
BotTROP is an advanced malware detection system designed for corporate networks, capable of identifying infected devices through network traffic analysis. This innovative tool leverages machine learning to tackle one of cyberspace’s most significant threats: botnets. Its proprietary algorithm detects patterns of synchronous activity in network traffic at the interface between the local network and the Internet. The system’s graphical output facilitates real-time threat detection, making it especially valuable for Security Operations Centers (SOCs).

While there are numerous malware detection tools on the market, most rely on previously identified Indicators of Compromise (IoCs), rendering them ineffective against unknown threats, particularly those utilizing unconventional communication protocols.
Here’s what sets BotTROP apart:
1. Artificial Intelligence
BotTROP employs a novel unsupervised machine learning algorithm that identifies signs of synchronous activity in both real-time and pre-captured network traffic. Its graphical presentation of results enables real-time threat detection, making it particularly valuable for Security Operations Centers (SOCs). Because BotTROP doesn’t depend on supervised machine learning, there’s no need for a training set, such as traffic generated by an unknown botnet. This capability has been validated in multiple experiments, demonstrating its effectiveness against unknown threats.
2. Network-Based Analysis
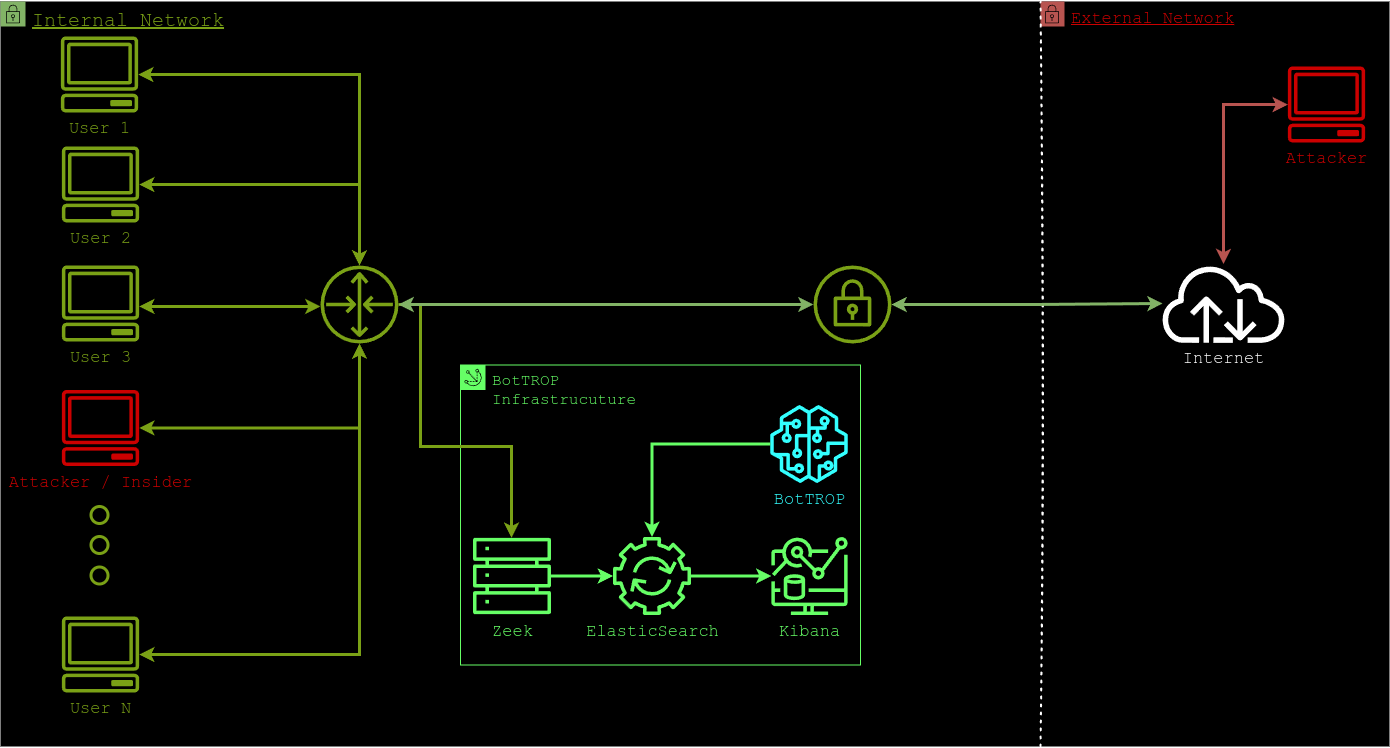
BotTROP requires no additional software installation on protected devices. The centralized architecture of BotTROP streamlines integration into corporate networks, removing the need for additional software installations on client devices. By concentrating on network traffic characteristics rather than its content, BotTROP effectively manages encrypted traffic as well. The tool has been extensively implemented and tested using both simulated and real network traffic.
3. Protocol-Independent Solution
The solution is protocol-independent, effectively managing any communication protocols that may be used by infected devices, which enhances its versatility in diverse network environments. By seamlessly integrating with various protocols, it ensures comprehensive visibility and control over all network traffic, regardless of the underlying technology. This capability allows for the swift identification and containment of threats, regardless of how they communicate, providing robust defense against a wide range of attacks. Additionally, its adaptability enables organizations to maintain security even as new protocols emerge or existing ones evolve. Ultimately, this protocol-agnostic approach strengthens the overall security posture, ensuring reliable protection against potential vulnerabilities.
4. Capability Against Encrypted Malicious Traffic
otTROP can detect malicious communications within encrypted network traffic by leveraging advanced machine learning algorithms to analyze patterns and identify potential threats without compromising user privacy. Its ability to distinguish between legitimate and malicious encrypted communications enhances overall network security, providing real-time alerts for administrators. Additionally, BotTROP adapts to evolving encryption methods, ensuring continued effectiveness against emerging threats. With the increasing prevalence of encryption in modern communications, these capabilities are crucial for maintaining visibility and control over network activities, ultimately mitigating risks associated with encrypted malware and fortifying the organization’s defenses against sophisticated cyberattacks.
5. Comprehensive Threat Defense
The solution provides comprehensive threat defense by effectively protecting networks from both external and internal threats, utilizing a multi-layered security approach that includes advanced detection and response mechanisms. By continuously monitoring network activities, it identifies and neutralizes botnets during creation phase before being used for cyber-atacks. This proactive stance not only safeguards sensitive data from cybercriminals but also addresses insider threats by monitoring user behavior for suspicious activities. Additionally, the solution incorporates regular updates to adapt to emerging threats, ensuring robust protection in an ever-evolving threat landscape. Ultimately, it delivers peace of mind for organizations by creating a resilient security posture against a wide range of attack vectors.
6. Proven Effectiveness
An experiment was conducted to detect both real and simulated botnets using network traffic that included:
- Actual traffic from the Military University of Technology in Warsaw.
- Network traffic generated by real malware, captured at the Czech Technical University in Prague as part of the Malware Capture Facility Project (MCFP).
- Network traffic generated by a botnet simulator alongside a legitimate traffic simulator.
- Traffic created by open source malware such as
An important experiment demonstrating the effectiveness of the BotTROP method involved detecting devices infected with open-source malware. The BotTROP method successfully identified all infected devices. The table below provides a summary of the experiment.
| Malware Name | Botnet’s size | Time range | Pakets’ count | Result probability |
|---|---|---|---|---|
| Powershell Empire | 4 | 14h 27min | 249 161 | 0.999 |
| Ares | 4 | 11h 36min | 828 770 | 0.985 |
| AsyncRAT | 3 | 12h 02min | 67926 | 0.639 |
| Badrats | 4 | 12h 04min | 347017 | 0.996 |
| Covenant | 4 | 12h 09min | 67101 | 0.841 |
| DeimosC2 | 4 | 12h 37min | 98267 | 0.702 |
| DaaC2 | 4 | 12h 37min | 98267 | 0.701 |
| GoDoH | 4 | 14h 44min | 22291 | 0.990 |
| HardHatC2 | 3 | 13h 48min | 20027 | 0.753 |
| Metasploit | 4 | 19h 33min | 2853 | 0.997 |
| Redherd | 4 | 18h 52min | 4514 | 0.997 |
| QuasarRAT | 4 | 12h 00min | 4122 | 0.819 |
| Sandman | 4 | 15h 57min | 114 007 | 0.999 |
| Shad0w | 4 | 11h 57min | 9532 | 0.816 |
| Ninja | 4 | 24h 04min | 308 479 | 0.994 |
| EggShell | 3 | 24h 00min | 263 | 1.0 |
| Godgenesis | 4 | 24h 00min | 201 | 0.938 |
| Havoc | 3 | 24h 00min | 265 626 | 0.986 |
| MiniC2 | 3 | 21h 28min | 2918 | 0.757 |
| PoshC2 | 4 | 24h 00min | 68265 | 0.894 |
| SecretHandShake | 3 | 25h 31min | 1572 | 1.0 |
| Silver | 4 | 24h 10min | 35084 | 0.798 |
| Vilian | 3 | 25h 31min | 3374082 | 0.856 |
| TrevorC2 | 4 | 17h 02min | 272 178 | 0.755 |
| TwitterBot (proprietary solution) |
How does BotTROP work?
The tool detects signs of synchronous activity in network traffic at the interface between the local network and the Internet. This synchronous activity can occur not only during an attack but also during the creation and management of malware, enabling threats to be identified even before the initial attack. This proactive capability allows administrators to take preemptive action, representing a significant advancement over previous methods.
Once group activity is identified, BotTROP not only pinpoints all infected devices but also, when integrated with the firewall, allows for the blocking of malicious network traffic specific to each infected machine—without disrupting legitimate traffic. The video below showcases a real-life example of how BotTROP detected Powershell Empire C2 malware.
Additionally, BotTROP is effective against unknown malware, such as TwitterBot, which utilizes the X (formerly Twitter) communication protocol.
Where can BotTROP be most beneficial?
BotTROP is fully capable of functioning in a production environment. Simply provide network traffic, which will be periodically analyzed by BotTROP’s proprietary artificial intelligence algorithm.
The tool also features advanced visualization of identified threats, enabling administrators to continuously monitor network traffic for malicious activity. Rapid identification is essential not only for detecting malware and mitigating its effects—such as data extraction or encryption—but also for preventing external control of infected devices and effectively eliminating threats from the network. To meet diverse needs, BotTROP is available in two versions: BotTROP-EDU and BotTROP-PRO. The BotTROP-EDU version is designed to support the education of administrators, helping them understand all functions and new opportunities. In contrast, BotTROP-PRO is the fully implemented version suitable for production environments where real-time analysis is essential.
Part of the software underlying BotTROP such as Zeek and ElasticSearch is widely used in other solutions, to protect networks. This widespread use makes BotTROP exceptionally easy to integrate with existing security mechanisms."
BotTROP - EDU